As a cyber security consultant for over 20 years now, I’ve observed a wide spectrum of maturity levels within organizations large and small. I’ve been engaged in over a thousand projects related to everything from firewall/IDS deployments to advanced red teaming services. As a result, I’ve become acutely aware of organizations’ weaknesses, gaps, and improvement opportunities related to cybersecurity. One area that has me especially concerned today is vulnerability management.
Today, vulnerability management is described as an organization’s cyclical practice to identify, measure, and remediate the vulnerabilities that present the most risk to the organization. Most organizations leverage a myriad of different technologies and processes ranging from commercial vulnerability scanners to home-brewed excel spreadsheets, to meet the program objectives.
The biggest challenge we are observing as an industry is that most vulnerability management programs are focused on vulnerabilities that don’t matter. Organizations are spending time, money, and resources on vulnerability remediation tasks that have little impact against a malicious attacker. This is not only inefficient, but it can also dangerously misconstrue the organization’s true risk – which is exactly why it is increasingly common for a malicious adversary to go from initial access to full-blown network compromise in minutes or hours without being detected.
In addition, most companies don’t understand the various levels of maturity related to vulnerability management and don’t understand how to apply a risk-centric model. Too many companies take the same approach:
- Scan all the things
- Patch all the things
- Rinse and repeat monthly
This “boil the ocean” approach accomplishes nothing. Nor does using severity levels as a risk-centric variable. Many organizations have thousands of critical severity vulnerabilities, with limited resources to mitigate them. They are unable to substantiate true risks to the environment based on more valuable variables like asset values, vulnerability exploitability, prevalence and age. Simply trying to remediate threats based on severity levels alone is inadequate.
Many organizations are struggling in regards to identifying and mitigating risks that a true malicious adversary or piece of advanced malware would leverage. These are vulnerabilities that are not going to show up in your vulnerability scanners. They include threats like wdigest cached credentials, token impersonation, and MiTM attacks. Many organizations attempt to fill this visibility gap by leveraging a “traditional” penetration test, another area which has major opportunities for improvement.
Traditional penetration testing is dead. The days of just breaking into an organization and showing how that was accomplished are over—or at least they should be. Organizations should expect and demand more. They should demand that a penetration test cover a wide range of probable attack vectors into an environment, not just one or two. They should require the penetration test to better evaluate the effectiveness of the investments and security controls within the organization. Overall, organizations need to derive more value from penetration testing.
One of the ways organizations can derive more value and visibility is by leveraging the MITRE Adversarial Tactics Techniques and Common Knowledge (ATT&CK) framework. I often describe the ATT&CK framework as a blueprint for every way a malicious adversary can attack and compromise an organization. It’s an inch high and a mile wide and covers the entire lifecycle an attacker will take, from initial access to data exfiltration and command and control.
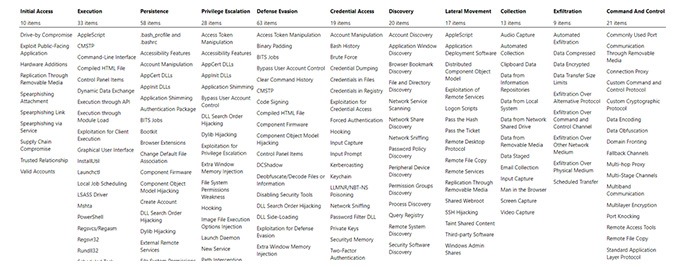
ATT&CK Framework
The challenge with the framework is its depth and complexity. Most organizations struggle to understand how to use it and where to prioritize. That’s where partnering with a vendor that is capable of understanding and operationalizing the framework is instrumental.
So, now that we have an understanding of the challenges, what can we do about it?
1. Understand Your Gaps
As mentioned earlier, having a solid understanding of your vulnerability management program’s maturity level is imperative. One of the ways to do that is by using the SANS approach. SANS has a very well-established maturity model that can help organizations assess where they are and what they need to do to increase their vulnerability management maturity.
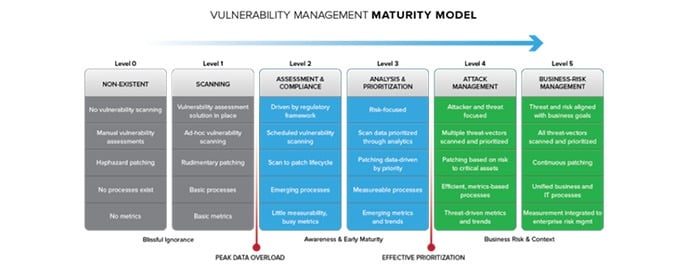
Vulnerability Management Maturity Model
Many commercial vulnerability management solutions are now geared towards a more risk-centric capability. By using other variables such as exploitability, prevalence, vulnerability age, and correlation with 3rd party threat intelligence sources, it is now possible to use these technologies to more effectively utilize an organization’s limited resources.
2. Align To The Framework
Internal red/blue teams and 3rd party penetration testing vendors need to align their activities to the framework. To get the wheels off the ground, it can be as simple as conducting different attacks in the ATT&CK framework and determining the organization’s ability to detect and prevent those attacks. In a more mature state, organizations can factor in the impact that countermeasures have, adding weighted variables to certain attacks based on the effectiveness of controls like EDR and IPS.
Over time, an organization can begin to measure their effectiveness trending, and work to consolidate the ATT&CK data into the organization’s global vulnerability management program.
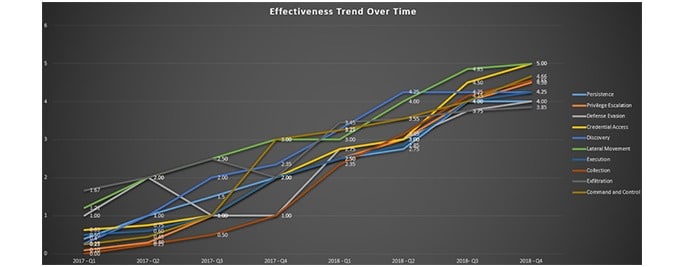
Effectiveness Trend Over Time
3. Focus On Prevalence
The CBI Advanced Testing Services (ATS) team leverages threat intelligence combined with the results of over 1000 engagements to help create our own custom prioritization attack path. This ensures we test our customers’ environments and control investments across the most critical areas. This results in a much stronger value derivative as compared to traditional penetration testing and helps our customers achieve more with the tools and technologies they already have.
The image below is an overview of the MITRE ATT&CK framework with some of the most prevalent attack paths and areas exploited across the lifecycle of the attack. These priority heat maps are based on attack vectors that malicious hacking groups have used and continue to leverage. In this example, we show what attack vectors groups like FIN8 and APT29 use. By prioritizing the framework against threats aligned to your company or industry, an organization can use their resources more effectively.
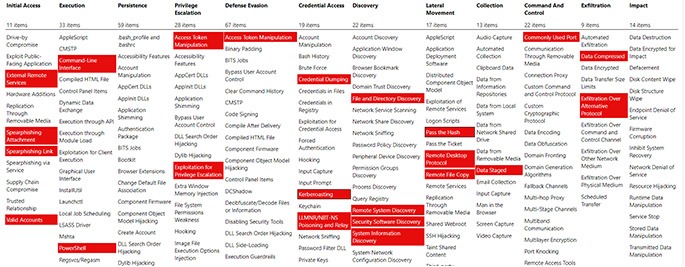
MITRE ATT&CK Heat Map
Via MITRE ATT&CK Navigator on GitHub: https://github.com/mitre-attack/attack-navigator
Identifying and preventing an advanced malicious attacker or a sophisticated piece of ransomware is not easy. Being great at security is not easy. To be great, organizations need to narrow in on key areas with laser-like focus. The MITRE ATT&CK framework can help establish that focus. This will result in a better return on an organization’s security investments by enabling it to tune existing controls more effectively, identify gaps where new solutions are required, and establish an overall enhanced capability to detect and thwart advanced attacks.




