Building a data protection program doesn’t happen overnight, and the frequently used comparison to a journey is accurate, with lots of ground covered before reaching maturity. So, what’s the best way to get started? Determining which direction to go.
An interesting research study shows that, like we learned from movies and TV, people lost in the woods, the desert, or the jungle (results were the same across settings) really do walk in circles, continually recrossing their own tracks. Study participants could only walk in straight paths with the sun or moon to guide them.
How does that apply to data protection? In today’s data-driven landscape, where data is both an asset and a liability and the risks and pitfalls are increasing, a clear view of the path ahead is essential. That’s where data discovery comes in.
What is data discovery?
From a cybersecurity perspective, data discovery is the process of locating and identifying data across endpoints, applications, clouds, and networks. It’s the cornerstone of data governance, providing visibility into your data landscape.
Using data discovery allows you to find your data assets, assess their relevance and sensitivity, and establish policies and controls for their management. Incorporated into your data governance framework, data discovery effectively monitors and enforces compliance with your data-related policies and regulations.
Why data discovery is important
Safeguarding sensitive information, ensuring regulatory compliance, and maximizing data value is paramount for all organizations and industries. But as technology evolves, so do the threats to data. Emerging technologies such as artificial intelligence (AI) pose opportunities and challenges to data management, and remote access amplifies data reach, flow, volume, and risk.
Data must be located and known to be protected. Data discovery is the essential first step on the longer path to ensuring the right data protections are applied consistently and effectively all the time.
How data discovery armors defenses against the most critical threats to data
- Cyber attacks: Data discovery helps identify vulnerabilities in data infrastructure so that the appropriate security measures can be implemented. These measures include encryption, access controls, and intrusion detection systems.
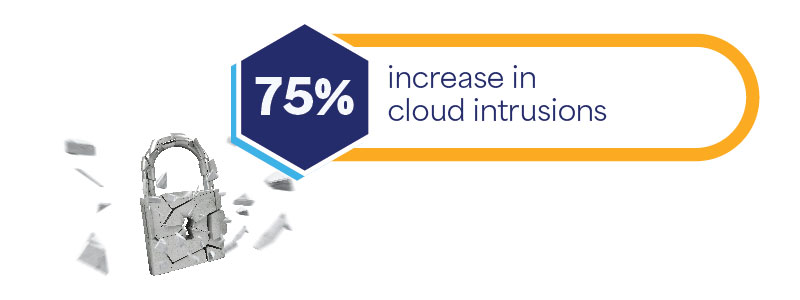
Source: CrowdStrike 2024 Global Threat Report
- Insider threats: What goes on inside your organization poses just as significant a threat to your data as attacks from outside. A malicious insider could exploit their access privileges to steal sensitive information or compromise your data integrity. Even when it’s not malicious, negligent employee actions also carry big risks. Data discovery tools detect unusual user activities and unauthorized access attempts, allowing you to take timely action to prevent data breaches.
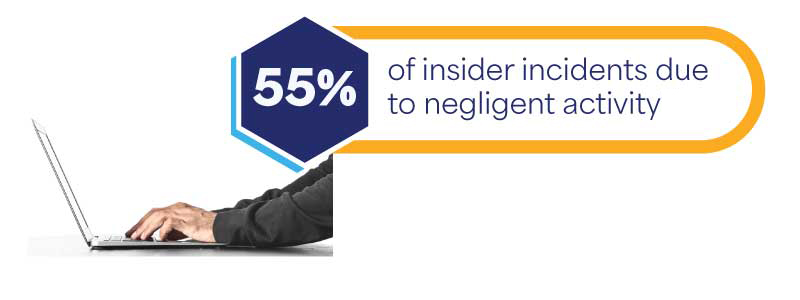
Source: Ponemon Sullivan Cost of Insider Risks Global Report 2023
- Ransomware: The summer months can cause a lull in activity, and ransomware gangs come and go, but ransomware attacks are still a growing threat. Data is always the hostage, with cybercriminals encrypting sensitive data and demanding higher and higher ransom payments for its release. Data discovery helps organizations identify critical data assets and implement backup and recovery measures to mitigate the impact of ransomware attacks.

Source: SANS Blog, January 15, 2024
- Regulatory non-compliance: Non-compliance with data protection regulations such as GDPR, HIPAA, and CCPA can bring hefty fines and legal penalties. Data discovery enables organizations to identify and classify sensitive data, ensuring compliance with regulatory requirements and mitigating the risk of non-compliance.

Source: Enforcement Tracker, Fines Statistics
How to implement data discovery successfully
1. Define objectives and scope: Clearly articulate the goals, objectives, and scope of your data discovery initiative, including the regulatory requirements you must meet and the data types to be protected.
2. Select the right tools: Evaluate and select data discovery tools using scalability, compatibility, and ease of integration with your existing infrastructure.
3. Develop a data classification framework: Establish a robust data classification framework to categorize data based on sensitivity, value, and regulatory requirements.
4. Engage key stakeholders: To ensure alignment across the organization, involve stakeholders from IT, security, legal, compliance, and other business units. Securing your organization’s data is a team sport. Success requires everyone to understand their roles, the risks, and the organization’s desired outcomes.
5. Conduct data mapping and take inventory: Identify where your data is created or sourced, where it’s stored, and find all access points across your organization, documenting metadata and ownership details as you go.
6. Implement scanning and analysis: Use data discovery tools to scan and analyze data repositories to identify sensitive data and security vulnerabilities.
7. Develop remediation strategies: Based on the findings from your scanning and analysis, develop remediation strategies that address your security vulnerabilities and compliance gaps and implement encryption, access controls, and data masking as needed.
8. Ensure continuous monitoring and improvement: Data discovery should be part of the larger flywheel of your data discovery program. Establish monitoring, evaluation, and improvement processes that ensure up-to-date policies and controls adapted to evolving threats and requirements.
Using artificial intelligence (AI) for data discovery
Artificial intelligence (AI) is an emerging game-changer for data discovery, enabling an automated, streamlined process for identifying and protecting sensitive information. AI-powered data discovery tools leverage machine learning algorithms to analyze vast amounts of data and identify patterns, anomalies, and potential security risks:
- Advanced data analysis: AI algorithms analyze unstructured data, such as documents, emails, and multimedia files, to identify sensitive information, even in complex and heterogeneous data environments.
- Predictive analytics: AI-powered data discovery tools predict potential security threats and vulnerabilities based on historical data and patterns, enabling proactive measures to mitigate risks before they escalate into full-blown data breaches.
- Automated remediation: AI-driven data discovery solutions automate the remediation process by identifying and implementing appropriate security controls and measures to protect sensitive data, reducing the burden on IT and security teams.
Final destination: Data protection maturity
Data discovery is your compass for navigating and mapping where your sensitive data lies and well-charted data is less vulnerable to breaches or regulatory scrutiny. As part of a holistic approach to data management and security, it keeps you on course in a complex data landscape, maintaining trust, resilience, and competitiveness in today’s digital age.
Experienced guidance is available to help you integrate data discovery with governance principles and clear your route to data protection maturity. Contact our Data Protection experts today to get started.
Other articles that might interest you:
Why Data Classification Matters & How to Inject It Into Your Security Strategy
The Art of Data Protection Blends Data Loss Prevention Into Business Operations





