As consultants on the Governance, Risk, and Compliance team at Converge, we’re often contacted by clients after every major cybersecurity or data breach incident hits the news. Their common question is, “Can this happen to us, and how can we be proactive?” They want to know if there is a checklist or spreadsheet they can use to give them confidence that they are “doing all the right things” and how to report it to senior leadership effectively. The quest for a one-stop solution is the holy grail in cybersecurity.
A client in the healthcare sector we worked with previously to perform several risk assessments reached out to us last week. Moments earlier, he had been questioned by the hospital’s board of directors after they learned of the United Healthcare cyber attack that crippled its ability to pay billions of dollars of health claims, affecting millions of patients and healthcare professionals. As we talked on the phone, we could hear the fear, uncertainty, and doubt about whether they would be the next breached company trending in the news. A recent study noted that ransomware kills one person each day in the United States.
Similarly, the director of cybersecurity of a medium-sized chain of fuel and convenience stores contacted me about how to apply their existing PCI DSS requirements more broadly throughout their infrastructure. She hoped to find a unified cybersecurity framework they could leverage to strengthen the overall security posture of their retail environment.
In those conversations, and when clients share concerns about cyber insurance coverage, we often discuss using the NIST CSF. Since cybersecurity insurance premiums are based on risk profiles, implementing a recognized cybersecurity framework like the NIST CSF can reduce an organization’s overall cyber risk exposure, the likelihood of successful cyber attacks, and the impact of incidents. It also shows insurers a commitment to proactive security and adherence to compliance requirements, which provide additional leverage in negotiating premiums.
Getting ahead of “doesn’t apply” frameworks
Providing a brief and valuable answer to these requests is elusive, even for those of us with years of cybersecurity experience. Each new iteration of emerging technologies—think mainframes and dumb terminals to microcomputers, floppy discs to networking, local area networks to the Internet, bare metal workstations and servers to virtualization, and datacenter-hosted virtual infrastructure to cloud instances—comes with complex challenges as unforeseen vulnerabilities are detected and exploited for malicious intent.
Until recently, there was no one-size-fits-all cybersecurity framework, eliciting common refrains from the clients we talk to who are responsible for their organization’s IT security: “This is so outdated” or “This doesn’t apply to us.”
Shifting momentum toward a universal cybersecurity framework
The tide is turning, however, in favor of guidance for implementing security controls and best-practice processes that help protect a diverse array of businesses and organizations from malicious activity. Until recently, the closest this came was through extensive knowledge sharing within the industry, including decades of documentation on the outcomes of using various controls for securing systems or data and learning from past mistakes.
In this third decade of the 21st century, the IT security industry is finally closer to agreeing on common control frameworks and best practices that apply across public and private sectors. A prime example of a recent leap forward is the significant revision of the NIST Cybersecurity Framework (CSF).
Revisions and additions to NIST CSF 2.0
Introduced in 2014 as “The Framework for Improving Critical Infrastructure Cybersecurity,” the Framework has undergone revisions to address evolving cybersecurity threats and challenges. NIST CSF 2.0 is the most recently released version. It incorporates user feedback and advancements in cybersecurity practices to move beyond its original focus on security for critical infrastructure to today’s version—an adaptable framework for businesses and organizations of all sizes, budgets, risk appetites, and tolerances.
Revision: Clarity and useability
Based on feedback from a broad spectrum of organizations that tested early revisions, 2.0 aims to enhance clarity and usability. Language, structure, and guidance improvements make CSF 2.0 more accessible and easily understood. These enhancements help organizations better communicate the need for these security controls across their business, particularly to non-technical personnel who gain more context and incentive to adhere to the security controls and processes. Increasing employees’ understanding of the value of these security controls and the consequences of not adhering to them helps organizations more effectively apply the Framework to their specific cybersecurity needs.
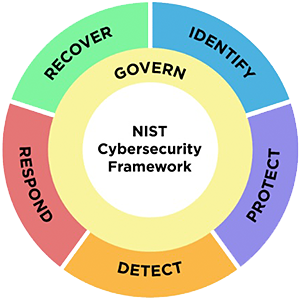
Example: Identity.Governance (ID.GV) and Identify.Business Environment (ID.BE) transitioned into the new Governance function. Govern.Organizational Context (GV.OC) includes directives for understanding how the organization’s mission must inform its risk management activities, including identifying and communicating the components of risk through the organization and covering the needs and expectations of internal and external stakeholders and legal, regulatory, and contractual requirements.
Image Source: NIST.gov
Revision: Portfolio and best practices
NIST also updated the CSF’s portfolio of security best practices and recommendations. As cybersecurity threats evolve, security processes must update to address mitigating those threats. NIST CSF 2.0 includes revised terminology stressing attention to detail and the importance of metrics for informed decision-making that reflects the latest understanding of protecting against and responding to cyber incidents, equipping organizations with contemporary cybersecurity strategies.
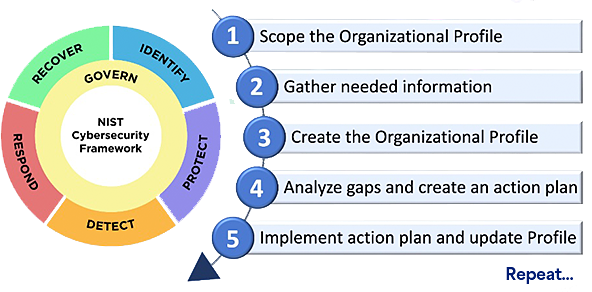
Example: Information on using Organizational Profiles to inform continuous cybersecurity improvement is expanded and provides improved guidance. A template for using the new Profiles is available from NIST.
Image Source: NIST Special Publications, Quick Start Guide for Organizational Profiles
Addition: Supply chain security
Data from significant security incidents in recent years indicate an upswing in threats due to organizations’ growing use of third-party services and vendors. The SolarWinds breach in late 2019 and early 2020 highlighted a major gap in technology security governance and management, impacting information security infrastructure across industries.
In response, NIST CSF 2.0 addresses supply chain risk through updated controls, explaining how all types of technologies rely on a complex, globally distributed, extensive, and interconnected supply chain ecosystem with geographically diverse routes and multiple levels of outsourcing. Supply chain controls nest primarily within the new Govern function with the Cybersecurity Supply Chain Risk Management category (GV.SC), detailed here.
The updated Framework helps organizations protect themselves against this growing cyber threat area by incorporating guidance on assessing and mitigating risks from upstream or downstream supply chain dependencies.
This updated guidance can be especially helpful for smaller organizations that rely heavily on third parties for technology, software, and hosting services. Enhanced supply-chain guidance for vetting, managing, and monitoring also helps ensure security and compliance with local laws and regulatory mandates.
Addition: Emerging technologies
New language addresses the risks of emerging technologies. CSF 1.1 didn’t mention either cloud or artificial intelligence. However, the new version specifically states that all areas apply to all information technology, the Internet of Things (IoT), operational technology (OT), and all technology environments, including cloud, mobile, and artificial intelligence systems.
For example, AI has cybersecurity, privacy, and non-technical risks, including legal and ethical implications. CSF 2.0 references the NIST Artificial Intelligence Risk Management Framework (AI RMF). Treating AI risks alongside other enterprise risks yields a more integrated outcome and greater organizational efficiencies. For organizations actively engaging in AI system development, the cybersecurity lifecycle controls in NIST CSF 2.0 provide crucial guidance on security considerations to address at each stage.
Example: CSF 2.0 controls for AI include: Identify. Asset Management (ID.AM) and Protect. Platform Security (PR.PS).
Revision: Compatibility with other cyber/privacy frameworks and regulations
CSF 2.0 provides improved integration with other frameworks and regulations. To help organizations comply with a broad range of regulatory requirements and security frameworks, CSF 2.0 addresses integrating, aligning with, and supporting other existing compliance standards and regulations, such as ISO 27001, COBIT, NIST SP 800-53, PCI DSS, HIPAA, and a growing list of privacy and protection laws and requirements.
Example: The overlap of cybersecurity and privacy objectives in certain circumstances is addressed and highlights its relevance for data breach regulations and cyber insurance readiness.
Organizations can use the NIST Privacy Framework with the Cybersecurity Framework to address the different aspects of cybersecurity and privacy risks. Additionally, NIST’s Privacy Risk Assessment Methodology (PRAM) has a catalog of example problems that can be used in privacy risk assessments.
Unification of best-practice security controls simplifies compliance efforts, strengthens overall cybersecurity strategies, provides a more cohesive approach to managing cybersecurity risks, and helps organizations streamline efforts across the different frameworks they may be following.
Governance empowers leadership to prioritize cybersecurity
While the Framework aims to be flexible and applicable across different sectors, organizations may face challenges implementing CSF 2.0. Smaller organizations or those with limited cybersecurity budgets may find it challenging to allocate sufficient resources for implementation, including financial and human capital, as qualified cybersecurity professionals are in high demand and command high salaries.
The breadth and depth of the guidelines can be difficult for organizations without mature cybersecurity programs or those with highly complex IT environments. These organizations may need to overhaul their cybersecurity policies, processes, and technologies to align with 2.0, which can be disruptive and costly.
Organizational must-haves for successful NIST CSF 2.0 adoption:
- Governance and a tone-at-the-top culture that prioritizes cybersecurity and understands its critical importance.
- Buy-in that overcomes opposition due to lack of awareness, resistance to change, or perceived inconvenience.
- Resources dedicated to continuous learning and awareness of the latest cybersecurity trends and technologies.
Effectively measuring the success of NIST CSF 2.0 implementation can take time and effort. Organizations must develop meaningful metrics and benchmarks to assess their cybersecurity posture. A clear understanding of their risk profile, risk appetite, and tolerance across senior leadership and business units, as well as the ability to measure security maturation over time, is required.
Overcoming security program challenges by industry sector
Although there is overlap, each business sector has challenges maintaining effective data security programs, many of which NIST has attempted to address with the changes in CSF 2.0.

K-12 & higher ed challenges
- Aligning with a diverse user base that includes students, faculty, and staff.
- Balancing security with academic freedom.
- Secure handling of sensitive student data.
NIST CSF 2.0 isn’t just a tool for big industries—it’s a lifeline for the education sector.
Consider this: Classrooms have transformed into virtual learning hubs, with students and teachers navigating remote access, virtual environments, and online collaboration tools. CSF 2.0 steps in to address the unique challenges faced by educational institutions, offering tailored guidance on improving security, protecting student data, and mitigating risks associated with these digital landscapes.
But the need for such guidance is starkly highlighted by real-world incidents. The Los Angeles Unified School District (LAUSD), the second largest in the US, fell victim to a ransomware attack in 2022. Refusing to negotiate, the District faced the release of 500GB of stolen data, including personally identifiable information, on the dark web. When New Mexico’s Las Cruces Public Schools faced a similar attack in 2019, they were forced to shut down internet service district-wide for over a week to rebuild 30,000 devices.
Even higher education isn’t immune. In 2019, over 60 colleges were targeted by an exploit that led to theft and denial-of-service attacks. These incidents underscore the urgent need for a flexible cybersecurity framework tailored to the education sector.
While CSF 2.0 may not provide granular controls for specific attacks, its flexibility allows institutions to prioritize and adapt controls to their unique risk profiles. Implementing CSF 2.0 controls could have mitigated the severity and rapid containment of the attacks at our example institutions.
As the spotlight on data privacy grows, CSF 2.0’s guidance on integrating privacy considerations into cybersecurity programs becomes invaluable. Educational institutions must safeguard sensitive student data and comply with regulations like FERPA and other privacy laws.
And as technology continues to evolve—with AI, virtual reality, and cloud computing shaping the future of education—CSF 2.0 offers guidance on managing cybersecurity risks associated with emerging technologies.
Many educational institutions already operate with limited resources, and that’s where CSF 2.0 has the greatest impact. By leveraging these targeted focus areas, educational institutions can holistically improve cybersecurity posture, protect student data, comply with regulations, and ensure the availability and integrity of critical educational services—all while embracing emerging technologies.

Restaurant & retail challenges
- Protecting customer data and payment information from data breaches.
- Securing ecommerce platforms and online transactions.
- Managing risks associated with point-of-sale (POS) systems and payment terminals.
CSF aligns with securing sensitive data in organizations of all size and industries, making it a valuable resource for restaurants and retail organizations.
Picture this: a bustling restaurant where the clinking of plates and laughter fill the air. Behind the scenes, their payment systems hum with activity, processing transactions with each order. CSF 2.0 steps in to ensure these systems are secure, protecting customer payment info from cyber threats.
Now imagine the kitchen is a whirlwind of activity as chefs create culinary masterpieces. But hidden risks lurk in the supply chain. CSF 2.0 offers guidance to help manage these risks, ensuring that every ingredient is safe and reliable.
And let’s not forget about customer data beyond the cardholder data already regulated by PCI DSS. From gamified loyalty rewards programs to online ecommerce ordering, it’s essential to keep name, address, email, and other PII protected, especially in the context of evolving privacy laws and large fines. CSF 2.0 provides strategies to integrate privacy protections into cybersecurity efforts, incident response, and breach readiness to maintain compliance with privacy and cyber regulations ultimately, but also to preserve consumer’s trust.
As restaurants and retail embrace new technologies like online ordering and mobile apps, CSF 2.0 offers insights to manage and secure these tools effectively. It’s a versatile framework that benefits any organization looking to enhance its cybersecurity posture and protect its systems and data from cyber threats.

Healthcare challenges
- Ensuring compliance with strict data privacy and security regulations, like HIPAA.
- Securing interconnected medical devices and the Internet of Medical Things (IoMT).
- Managing risks associated with remote patient monitoring and telemedicine services.
- Defending and immutable recovery against ransomware and non-disruption when providing medical care to patients.
In the realm of healthcare, managing cyber risk is paramount. It’s no longer just about meeting HIPAA requirements and safeguarding patient data; it’s about fortifying defenses against a multitude of threats, with some hospitals completely paralyzed by the never-ending bombardment of ransomware. Enter CSF 2.0. Its controls offer a robust framework to bolster risk management beyond HIPAA mandates and complement existing security standards like HITRUST.
But why are healthcare facilities such enticing targets for cybercriminals? A sprawling, interconnected, and complex medical services organization comprised of multiple Level 4 hospitals designated as advanced trauma life support and emergency services, dozens of outpatient surgery centers, and hundreds of clinics offer plenty of enticement. Patients’ lifelines are literally dependent on cutting-edge, multi-million-dollar medical technology systems that generate millions of patient health data (PHI) records in real time. It’s a literal goldmine for those with malicious intent. Factor in rotations of overworked doctors and nurses relying on records from the previous shift, highly interconnected systems, and widespread use of wireless tech, and attackers now have the perfect target to hold hostage for a maximum ransom payout.
The stakes couldn’t be higher. Any breach could lead to delays in critical care, exposure of sensitive patient information, and substantial financial burdens to regain control. That’s why resources like NIST’s CSF implementation guidance for healthcare are indispensable, offering multi-layered defenses that safeguard patient well-being.

Manufacturing challenges
- Identifying all ways to secure industrial control systems (ICS) and operational technology (OT) environments.
- Managing supply chain and third-party vendor risks.
- Implementing cybersecurity measures for connected devices and industrial IoT.
In the fast-paced world of manufacturing, where supply chain and delivery times are paramount to downstream industries in practically all industry sectors as well as military defense systems, it goes without saying that cybersecurity is essential. Traditionally, the focus has been on meeting industry standards and regulations, but threats now extend beyond these mandates. A simple shortage in manufacturing of microchips, bearings, or parts can have major economic impact—affecting not only the availability of consumer goods but also skyrocketing inflation.
Manufacturing plants, with their intricate networks, conveyor systems, robotic machines, and industrial control technologies, are all prime targets for cyber attacks. From supply chain disruptions to intellectual property theft, the stakes are high. Implementing robust cybersecurity controls is crucial for mitigating risks, bolstering resilience, and maintaining a competitive edge in today’s digital landscape, which is where CSF 2.0 can help offer a comprehensive approach to risk management tailored to manufacturing’s unique challenges.
Expanding NIST CSF into small and medium-sized businesses (SMBs)
A treasure trove of guidance within CSF 2.0 is also right for small and medium-sized businesses (SMBs). But here’s the catch: these businesses often operate with limited resources, making it tough to dive deep into cybersecurity measures. So, how do they unlock the benefits hidden within the guidance? Like bringing in a home inspector before purchasing a home, bring in a CSF 2.0 security consultant to assess your current state. You’ll get a tailored roadmap on what needs to be fixed and prioritized and uncover any showstoppers.
Picture an SMB or medium-sized business with people and budget resource constraints focused solely on running business operations and driving customer satisfaction. Partnering with a seasoned security consultant helps them chart a course for cyber maturity that enables executive support and budgeting, supports a cybersecurity culture, and prioritizes actions based on the risk assessment outcomes.
Working with the right consultant brings more than just guidance; they are a trusted ally and partner, armed with specialized knowledge and experience. With their help, the SMB adapts and adjusts to the ever-changing cybersecurity landscape, navigating the twists and turns with confidence. As they journey together, the SMB implements effective cybersecurity that ensures their business stays safe and operational.
Empower your organization with NIST CSF 2.0
Working with a cybersecurity partner already experienced with the Framework, its revisions, and your industry speeds implementation and improves the quality of the process.
Converge can help you tailor an implementation plan and roadmap aligned with your organization’s business objectives, regulatory requirements, and risk tolerance. Contact us today to speak with a consultant.