A well-known quote says a “rose by any other name would smell just as sweet.” That may be true for some things, but it leaves too much to chance for cybersecurity. Establishing known identities is crucial to securing users, data, and devices.
Identity and access management (IAM) is a core component of cybersecurity with a broad arc encompassing several key areas. With multiple vendors providing software and services related to IAM, the definition in the security marketplace can change depending on each vendor’s specialty. Some lean heavily toward the provisioning aspects of access, while others lean toward authentication and authorization.
The noise of competing messages can make it hard to know where to start building or augmenting your IAM program and identify what is most important to your organization.
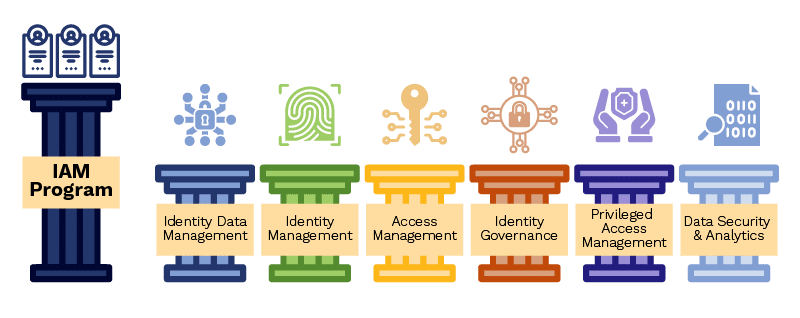
The Seven Pillars of IAM
The core intent of identity and access management is to ensure that the right people and things have the right access to the right resources at the right time from the right place. Technology plays a strong supporting role in achieving this, but knowing and understanding the fundamentals of IAM should come before implementing solutions.
These seven pillars form the arc of IAM across an organization:
- IAM program: Organizational approach applied by executive stakeholders and subject matter experts to IAM business drivers, technologies, and processes.
- Identity data management: Control and management of identity-related data, the systems housing that data, and processing of that data in all business areas.
- Identity management: Account administration addressing user life cycle, self-service management, and entitlements.
- Access management: Support for authentication mechanisms, such as single sign-on, multifactor authentication, federation, and password management.
- Identity governance: Policy-based activities that define, enforce, review, and audit IAM functions and compliance.
- Privileged access management: Processes and technology controls for elevated permissions, such as administrator privileges.
- Data security and analytics: Management of unstructured data, data identification and classification, and user analytics supporting data security programs.
Building IAM as Your First Perimeter
Putting the IAM program in the first pillar position isn’t by chance. Several point-specific technologies will likely be implemented as part of your IAM approach, but IAM isn’t a technology. It’s a program initiated and managed as part of conducting business. Before buying and implementing any application, you need to build your program. It’s the load-bearing pillar of all other IAM initiatives.
We’ve all seen security breaches in the headlines—massive amounts of customer data exposed or an organization forced to shut down because of a ransomware attack. Structuring your identity as your first perimeter can help keep your organization from being the next big news.
Understanding that IAM is a program, not an application, allows for a comprehensive approach. IAM touches every part of your organization, impacts how you do business, guides onboarding and offboarding users, and directs how your organization interfaces with employees, contractors, vendors, and customers. Embracing IAM throughout the entire organization is crucial.
IAM and Executive Leadership
Adopting IAM in an organization begins with executive sponsorship. That doesn’t mean that this program falls under a particular executive. Instead, it means that the executive body owns the success and effectiveness of the IAM program. Your leadership needs to consciously realize that IAM is a critical component of your business’s continued competitiveness and ability to go to market.
Because implementing an IAM program touches every aspect of your business, executive buy-in and support are crucial to aiding cooperation throughout the company. Executive ownership helps clear obstacles that may arise in your path to implementation. The larger an organization, the more likely silos have formed and claims staked on certain areas of the business. These “fiefdoms” can have “rulers” who are very protective of controlling all aspects of the areas they have deemed theirs. IAM will intrude on their space, and it will take strong executive leadership committed to the program to break down the barriers.
Steering IAM Success
Experience with dozens of IAM program initiatives shows that successful IAM programs include an active, engaged IAM steering committee with representatives throughout the organization.

The composition of the committee will vary by organization but should include these roles:
- Executive sponsor
- IAM program director
- IAM architect
Delegates from other groups impacted daily by IAM should be included, such as:
- Human resources
- Legal
- Sales
- Customer service
- Project management
- Accounting/finance
- Production
- Research and development
- Operations
Navigating IAM Standards
This committee sets the technical direction of the IAM program and is tasked with the timely, secure evolution of the program to meet your business’s changing needs and opportunities. One of the first goals of this committee is to develop standards for how the organization’s systems, applications, and processes integrate with the IAM program and technologies.
These standards should include:
Application integration and authentication
- Where identity information can be physically stored
- Multifactor authentication (MFA) and single sign-on (SSO) requirements
Onboarding/offboarding
- Policies and procedures
- Emergency termination protocols
Access review schedule and process
- Schedule for standards review
- Separation of duties policies
- Micro-review policies
Charting Critical Integrations
Next, the steering committee should identify and prioritize applications and business processes related to IAM solutions.
That prioritization process could look something like this:

Level 1: Mission-critical applications and processes essential for business operation. IAM technologies must work with and not interrupt these applications or processes. Ensure compatibility when reviewing and choosing a solution.
Level 2: Applications and processes necessary for some portions of the organization to operate. These technologies may be department- or subsidiary-specific, critical to the functions of a department but not the organization. Best efforts to integrate these with IAM solutions should be made, but app or process modifications may be necessary to fit.
Level 3: Non-critical applications and processes. These should conform to the standards published by the IAM steering committee. Updating or replacing an application or process may be needed to comply.
The steering committee should set and adhere to regularly scheduled meetings. This time can be used to share and review any business or technology changes that could impact the performance of the IAM program. A steering committee member should also be part of the change control board so that IAM standards compliance factors into changes in the organization’s technology footprint.
Shine a Light on IAM Importance
Operating in the shadows isn’t how you want your IAM program to run. Communicating frequently as the program develops and matures is essential for successful implementation. You want everyone in the organization to understand what you are doing, why you are doing it, how it impacts them, and its role in keeping the organization healthy and secure. Users without the necessary information may choose easy rather than right or safe, subverting your program efforts.
Successful programs use one or more of these communication methods:
- Internal website/intranet: Use to share and update information that is helpful and available for all organization members, including standards for integration, user guides, and FAQs.
- Direct communication: Periodic, direct communication with the organization’s line of business owners provides an opportunity for feedback on how the IAM solution is helping or hindering their daily functions. Their feedback is critical in maintaining the organization’s commitment to the IAM program.
- Email: Use broadcast emails to reiterate the important points of your program.
“Tell them what you’re going to tell them, tell them, then tell them what you’ve told them.” This old adage is an excellent strategy for your communications. Remember that effective communication travels a two-way street. Actively listening to challenges and suggestions also plays an important role. The more users understand what to do, why it’s important, and how they are part of the process, the easier success will come.
The Path Forward
Doing this groundwork first puts the right stakeholders in place and provides the information to compare and evaluate IAM solutions effectively. It helps you avoid the costly mistake of choosing a solution that doesn’t fit your technical infrastructure or the way your organization does business.
Converge has a collaborative advisory approach, decades of experience, and partnerships with leading IAM solution vendors. Talk with one of our IAM experts to see if our relentless focus on cybersecurity is a good fit for your organization.