Zero trust is no longer just a theoretical security buzzword. Since the onset of the pandemic and the demise of the network-based perimeter, more organizations than ever have been moving to zero trust to more tightly lock down assets and resources.
More than two years into this transition, we wanted to understand more about how organizations are doing at implementing zero trust and how it is impacting their security posture. With the help of Check Point, we collaborated with Ponemon Institute on a study to find out. The result is our new report, “The State of Zero-Trust Architecture in Organizations,” which offers insights into why organizations have adopted a zero-trust approach, the security and other benefits they’ve experienced, as well as obstacles they have faced along the way.
The study looked at organizations that have embraced zero trust or are in the planning stages. Surveyed organizations ranged in size from 1000 to over 75,000 employees. Here are five of our takeaways from the report.
(1) Organizations that implement zero trust experience productivity benefits in addition to security benefits.
51% of surveyed organizations have adopted a zero-trust network architecture. The most often-cited reasons for doing so were to reduce connectivity issues and improve user experience (52%) and to reduce the difficulty of provisioning new users and decommissioning departing users (51%).
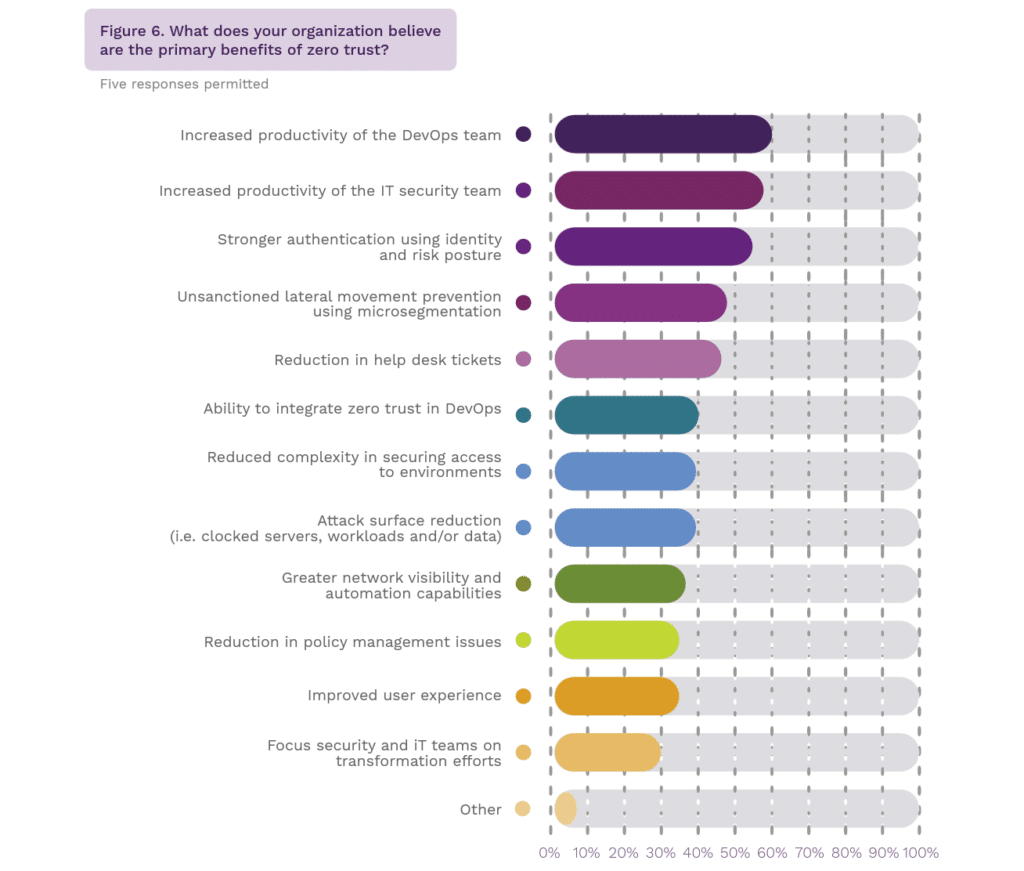
When it comes to the benefits of zero trust, the top two advantages cited by respondents were increased productivity of DevOps teams and increased productivity of IT security teams. These benefits were followed by stronger authentication and lateral movement prevention.
It’s interesting to see that the top reasons for moving to zero trust and its top benefits are not primarily security-related. Zero trust has the benefit of increasing efficiencies not directly related to security, while at the same time improving security. That’s a big plus in the security world, which has traditionally been seen as a hindrance to both user experience and productivity.
(2) Zero trust restricts lateral movement and reduces attacker dwell time.
The use of zero trust improves the ability to minimize risks from dwell time and lateral movement. 53% of respondents agreed that zero trust has reduced attacker dwell time in their networks, and 56% agreed zero trust is very effective or highly effective at eliminating lateral movement between users and servers. This is especially important because if a system is compromised, only 39% of respondents are confident that their organization knows which critical business services could be impacted or how an attacker could use that system to move laterally.
In addition, 65% of respondents say zero trust makes their organizations very or highly effective in authenticating, authorizing, and inspecting all traffic flow at all times to ensure malware and attacks don’t sneak in accidentally or maliciously.
(3) Aligning technology with a zero-trust strategy is a challenge for many organizations.
The road to zero trust is not all paved with gold—technology proves to be an obstacle for many organizations. Only 42% of respondents claimed that their current security tools are very or highly aligned with their zero-trust roadmap. Only 50% said they are very or highly effective at determining which existing security technologies can continue to be used, and 54% said they are very or highly effective at prioritizing which new technologies to acquire.
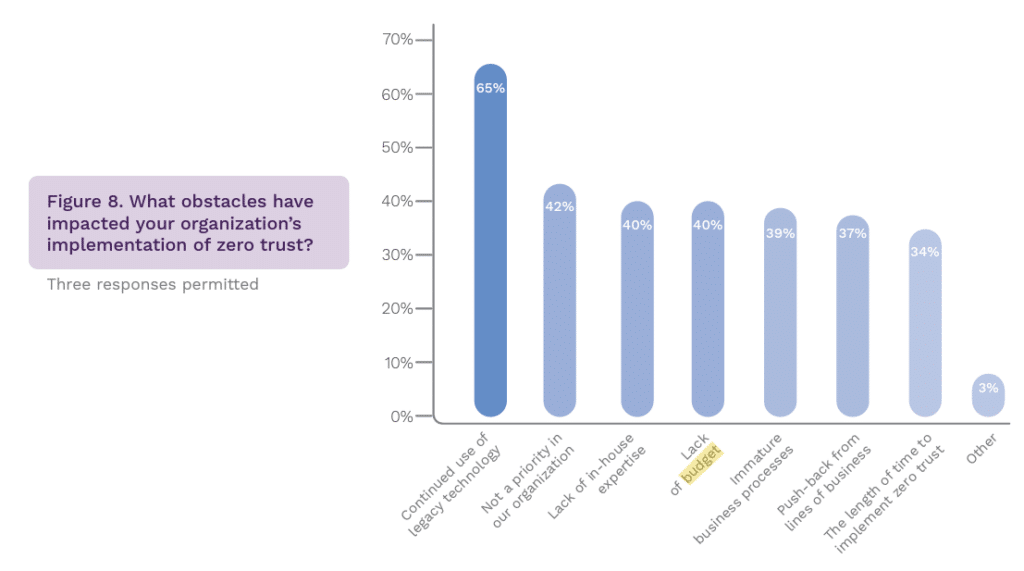
The continued use of legacy technologies was the most commonly cited obstacle to zero-trust implementation (65% of respondents). In addition, 50% of respondents said their organizations are still very or highly reliant on perimeter security.
(4) Quantifying and tracking the benefits of zero trust is important in achieving maturity.
The research reveals organizations’ varying levels of zero-trust maturity. 27% of respondents claimed their organizations are in the mature phase of zero-trust adoption, with zero-trust activities fully deployed across the enterprise. 33% are in the full adoption phase with zero-trust activities mostly deployed. Of respondents in the mature or full adoption stage, 71% said it took 5 to 7 years or more to achieve.
66% of respondents also say their organization’s IT security team attempts to quantify and track how zero trust improves security posture with either a full or partial metrics program. The top three metrics used are reduction in the number of data breach incidents (65% of respondents), reduction in the number of known vulnerabilities (63% of respondents), and reduction in the number of threats (57% of respondents).
Regularly informing senior leadership about the effectiveness of the program as measured by these performance indicators can help garner executive support to secure the resources needed for full zero-trust implementation.
(5) Lack of budget and in-house zero-trust expertise hinder implementation.
Lack of budget was cited as an obstacle to zero-trust implementation, with 40% of respondents citing it as an issue. According to the research, the average annual IT security budget is $32 million, with an average of $2.4 million dedicated to organizations’ zero-trust strategy.
Lack of expertise also presents a constraint, according to 40% of respondents. Although 68% of organizations have staff dedicated to zero trust, 75% of respondents say their staff does not have zero trust certifications. 76% of organizations handle their zero-trust implementation by outsourcing at least some zero-trust activities to a third-party organization.
Download the full report to learn more about organizations’ journeys to zero trust, including:
- The top components making up organizations’ zero-trust security models
- Organizations’ top obstacles to detecting cyber attackers within their networks
- How organizations handle zero-trust activities in-house versus outsourcing
- The effectiveness of zero trust in reducing cloud security risks




