The ever-changing threat landscape is a popular topic for cybersecurity resources. An astonishing number of articles, whitepapers, and podcasts reference this in one way or another. And it’s true, shifting and emerging attack vectors and methods are a reality for cybersecurity professionals.
But the most significant risk to an organization’s security posture isn’t necessarily tied to an innovative, new attack method. The Converge Cybersecurity Red Team’s review of 2022 shows that what is old is still relevant and that classic attack methods are just as successful as ever.
Converge Cybersecurity conducted 129 penetration tests on 14,436 assets last year, helping organizations across verticals find and fix their network, application, and physical vulnerabilities.
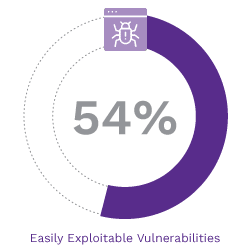
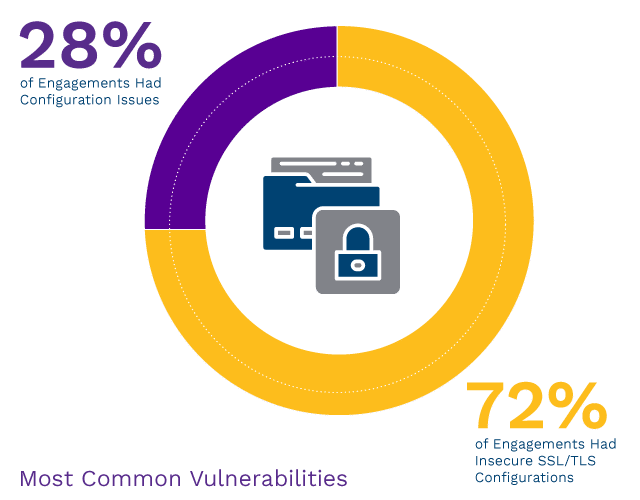
Easily exploitable vulnerabilities were found in 54% of our engagements. Credentials continue to be predictable, stored insecurely, reused, and shared. Default usernames and passwords are still common. Overprivileged accounts and misuse of accounts frequently enable quick privilege escalation and lateral movement. Man-in-the-middle (MitM) attacks against common services are routinely successful on internal networks. Systems are not consistently hardened. Patches are missing. In short, malicious adversaries have not needed to change their tactics or enhance their skills to achieve their objectives in most networks, and common vulnerabilities continue to be abused to obtain unauthorized access to systems and data. The good news is that most of these can also be easily remediated.
Key Findings Summary

Web, API, and Mobile Applications
Remote access has moved most business functions and tools online, creating a fertile hunting ground for attackers. They haven’t let the opportunities pass them by. Web application attacks account for 26% of all breaches. No matter the size of an organization, one security flaw left unresolved is all that’s needed for an organization’s data to end up on the Internet. Source code analysis, integration of security checks in the continuous integration and continuous delivery (CI/CD) pipeline, and regular application-layer penetration tests can expose these flaws and enable remediation.

Email is still a top attack vector for initial access. Phishing tactics appeal to human greed, fear, and curiosity to lure victims into clicking, downloading, and responding to malicious methods. Security awareness training is essential but needs to be supported by foundational efforts. Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-Based Message Authentication, Reporting, and Conformance (DMARC) should be leveraged to reduce risk, along with email security gateways with link scanning, and strong file type and extension filtering capabilities.

Configurations and Patching
Unpatched vulnerabilities and improper configurations continue to plague organizations of all sizes. Attackers are current on patch releases and top misconfigurations. Delaying patching because of business disruption concerns can lead to this exact effect when leveraged by an attacker. Organizations should identify and remediate existing issues and implement patch and configuration management into daily security operations. Technologies can help achieve consistent patch levels and configuration hardening, and segmentation of network assets further reduces risk.
Passwords
Passwords and credentials are the keys to digital life—giving access to critical data and functions. Weak passwords, reused credentials, and, yes, even default credentials were top exploitable vulnerabilities in 2022. Our number one failed test case is the abuse of legacy Windows protocols that can be poisoned to capture and relay hashes in a pass-the-hash attack. These hashes are often susceptible to cracking due to poor password hygiene, providing valid credentials to reuse in the environment. Organizations should implement tactical and strategic measures to protect credentials. Leveraging password management tools can create and rotate unique local administrator passwords. Implement password filters to reject weak passwords, phrases, or terms related to the company brand, as well as words commonly used in passwords, such as “password” and months of the year.

Most exploited network vulnerabilities
Our approach to penetration testing emphasizes manual techniques to leverage our testers’ ingenuity and skills combined with a bit of automation. Some vulnerabilities have no known exploit code or technique or require suitable positioning on the network, making them less open to manipulation. We help our clients prioritize the vulnerabilities uncovered in their environment so they can remediate those most likely to be abused first.
This list reflects the top test cases exploited by our team in 2022, but our team says they successfully take advantage of most of these same vulnerabilities year after year.
- Storing credentials in clear text without encryption
- Reusing local administrator credentials
- Missing patches; for example, MS17-010 for Microsoft Windows SMB Server was released in 2017 but still hasn’t been applied in many instances
- Using default credentials
- Use of default Windows legacy network protocols that enable poisoning and MitM attacks
- Insecure or incorrect implementation of IPv6 traffic routing protocols allows MitM exploits
- Allowing unnecessary and excessive use of local admin privileges
- Use of Cisco Smart Install
Are these emerging network vulnerabilities?
What about risks that aren’t rinse-and-repeat, year after year? We asked our network penetration testers to dive deeper into their data and personal testing experiences. We uncovered abused network-layer vulnerabilities that weren’t on the list above but were increasingly successful for our testers later in the year.
These findings could indicate emerging vulnerabilities or subsets of existing ones. Our testing team noted the abuse of common Active Directory misconfigurations, such as Kerberos and Active Directory Certificate Services (AD CS), as a frequent source of success in privilege escalation.
Steps for remediating network risk
Our network testing experts recommended these steps to counter-act the efforts of malicious actors:
| Enable Server Message Block (SMB) and Lightweight Directory Access Protocol (LDAP) signing to prevent password relay attacks. |

| Enable Extended Protection for Authentication to remediate AD Certificate Services abuses. |
| Use network segmentation for more granular control of internal access to system services. |
| Disable legacy Windows broadcast protocols to reduce the attack surface for poisoning and MitM attacks. |
| Separate admin from daily-driver accounts and apply the principle of least privilege so that users only have the access they need to do their jobs and no more. |

| Secure your local Windows admin passwords using the Microsoft Local Administrator Password Solution (LAPS) to mitigate password reuse. |

| Deploy a Microsoft group Managed Service Account (gMSA) to limit service account password storage in the clear. |

| Enable Windows Credential Guard to reduce the attack surface for pass-the-hash and pass-the-ticket adversary techniques. |
Most exploited web application vulnerabilities
The average SOC team receives approximately 10,000 alerts per day for security alone. The increasing number of endpoints, complex security stacks, web applications, APIs, and remote users feeds this tsunami of alerts. It’s no wonder that most security teams have alert fatigue, and it further pinpoints the value of penetration testing to detect vulnerabilities that go unnoticed and unremedied.
Web applications are the leading attack vector for security incidents and breaches, and 56% of bad actors’ payload targets are web app servers.
Those findings hold with what we’ve seen in our testing. Unintentional exposure of API keys was especially prevalent during our application testing. Searches of Github during both application and network-based penetration tests uncovered exposed API keys for key company resources, including Azure storage buckets and general access keys, AWS S3 buckets, Google Cloud Platform storage buckets, and Firebase databases. This exposure often enables anyone with access to the application to enumerate client or consumer information.
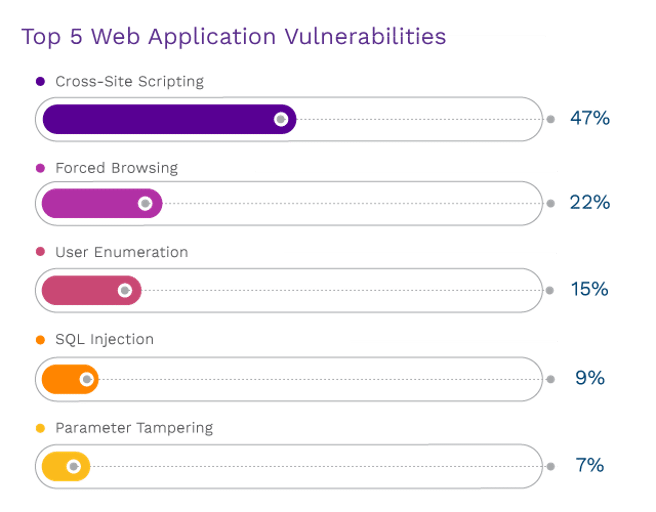
During 2022, we saw these top five vulnerabilities, all with a degree of exploitability and heightened severity. All sit within the OWASP Top 10. What we see in our clients’ environments aligns with the shift in the industry. Broken access controls are rising, while injection attacks are consistently present.
Protecting your web application layer
Application-layer attacks can be sophisticated and cause tremendous damage quickly. Although organizations depend on applications to run or support their business, more is needed to validate and reinforce application security.
Most of the severely crippling attack paths used to access restricted data are lower severity vulnerabilities such as information disclosure, user enumeration, no rate limiting on logins, and abuse of “forgot password” functions. A skilled eye is recommended so that risk potential factors into remediation efforts. Implementing secure design and coding practices that identify these issues early in the application life cycle helps prevent these vulnerabilities from being introduced.
Combinations of vulnerabilities can lead to chained attack paths useable without credentials to access restricted data on public applications, quickly scaling the risk from zero to 100.
Automated application testing solutions exist but haven’t matured enough to detect more sophisticated threats. Combining the broad coverage and efficiency of automated tooling with the manual testing of a skilled application security expert produces the best results in our experience. We recommend that organizations introduce continuous, manual testing into their security programs.
Exploited physical vulnerabilities
In the aftermath of COVID, many businesses have implemented hybrid and return-to-office policies for their employees. We saw a significant increase in the number of physical tests we conducted in 2022.
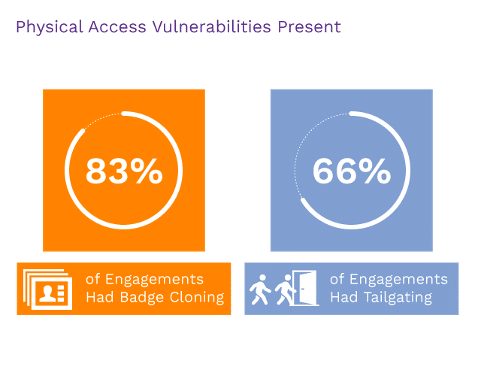
Physical badge cloning is a top physical vulnerability and something that some clients are surprised to find in their testing results. Some organizations believe their badge systems are HIRF/encrypted, but testing shows that is not the case.
And if entry wasn’t gained with a cloned badge, our team had success with tactics like under-door bypasses and infrared hacks. We only failed to gain entry on two occasions; both were medical facilities.
Human fallibility isn’t just for emails and clicking links. Social engineering, done with confidence, can convince employees to provide access to systems and restricted areas. Our on-site testers were challenged in only two cases, something that increased security training can help overcome.
Fortunately, we see an uptick in using NAC access controls, so clients are better protected from malicious connections to open network jacks in both shared and private areas.
What does this mean for 2023?
Malicious actors are capitalizing on many organizations’ rush to the cloud in response to the pandemic. It was a necessary move to continue business operations, but it produced security gaps that can be hard for security teams to see without the right tools and testing.
Comprehensive penetration testing provides valuable insights into vulnerabilities that have gone undetected. Uncovering areas that need improvement or mitigation to lower risk helps identify and address potential vulnerabilities so that organizations can prioritize security improvements accordingly. A penetration test delivers actionable remediation guidance that is both tactical and strategic to reduce risk to organizationally accepted levels. If you’re ready for a deeper look into your environment, reach out today to get started.