Another year is behind us, a year filled with remarkable advancements, jaw-dropping breaches, and the good guys still struggling to keep up with the bad guys. Before jumping into how 2024 may shape out or diving right into the doom and gloom of what went wrong in 2023, let’s first start by reflecting on some of the positive attributes of 2023.
· Enhanced investment and awareness: We here at Converge feel overall that public and private industries have finally realized the impact of a breach and the advancements in the global threat landscape. We’ve seen more refined budgets, direct C-suite involvement, and progress made with public education initiatives.
· Technology advancements: 2023 was remarkable for many organizations. We’ve witnessed first-hand organizations advancing through zero-trust programs, enhancing data protection capabilities, AI and machine learning maturity, and more adoption of cloud security solutions that can actually make a difference.
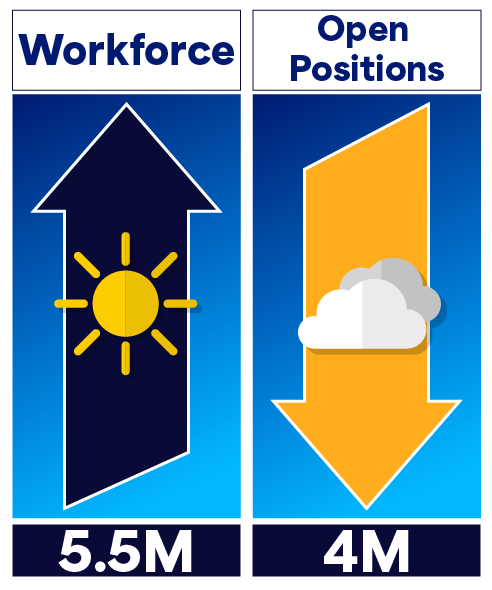
· Talent and diversity. The cybersecurity workforce grew to an estimated 5.5M professionals , and women in cybersecurity roles averages 24% globally. We certainly have work to do there, but the momentum is strong.
We’ve also witnessed what we believe to be a milestone shift in how we’re educating our younger workforce. Even though the global cybersecurity workforce grew to the highest level ever recorded, we are still facing down the barrel of 4M unfilled cybersecurity jobs. Yet one of the positive attributes we observed in 2024 was a shift in how we are training and educating our next generation of cybersecurity specialists. Better paths for hands-on training, more vocational efforts, a myriad of free support programs, and an overwhelming outreach of support by our community to those that need it, are improving our odds to successfully meet the need for cybersecurity professionals.
Looking ahead for 2024
2024 will likely result in a similar dynamic of shifting strategies from adversaries, advancements in technologies, increased regulation, and big breaches. As an organization with hundreds of cybersecurity evangelists and thought leaders, we’ve collaborated on what we may expect in the coming year.
Reliable forecasts are hard to come by in weather and cybersecurity and unknown variables will shift our path in the months ahead. There will always be challenges to face and opportunities to make the most of. Our lists are intended to help align your focus for both.
Unfavorable conditions likely to persist

Ransomware is here to stay
The number of ransomware victims in 2023 surpassed those of 2021 and 2022 combined. In an industry where change is constant, one thing we can count on is that ransomware is here to stay.
As long as adversaries continue to cash out, this monetized attack framework will only evolve and advance. Ransomware as a Service (RaaS) will become more prevalent. The usage of initial access brokers (IABs) will increase, the extortion techniques and methodologies will continue to develop, and malicious adversaries will absolutely pounce on leveraging AI to their advantage.
Organizations must push towards more effective, earlier detection, threat modeling focused on probable TTPs, and the capability to dramatically advance security awareness testing and training.

AI weaponization (deepfakes) increases
While on the topic of ransomware and how adversaries will capitalize on AI, deepfake fraud attempts were up 3000% in 2023. While the geopolitical landscape and upcoming US elections are ripe for leveraging AI for malicious intent, the adversaries will profit from using AI in the private sector.
Our assumption, based on the current state of AI maturity, is that we will likely see an increase in attacks through deepfake audio first (think fraudulent wire transfers). Over time, we’ll see deepfake video technologies advance to the point that threat actors leverage it to impersonate users within an organization. Imagine an adversary jumping on a Zoom/Teams call with their targets to compromise them and gain an initial foothold.
Deepfake detection technologies are just not there yet to effectively combat this threat. Organizations should weave deepfake education into their security awareness training program, conduct threat modeling to identify how their organization would likely be targeted by deepfakes, and then determine what controls, if any, can be leveraged to build as much awareness and detection capabilities as possible.
Adversaries will target AI resources in GPU farming
So, how do adversaries get the powerpack resources needed to run large generative AI attacks? By targeting access to AI resources such as GPU farms. There is a tremendous amount of GPU horsepower out there for the taking—tenants of large cloud service providers (CSPs), the CSPs themselves, cryptomining endpoints, and organizations running on-prem GPU cluster farms. It’s a feasible assumption that adversaries won’t want to invest their own cash, simply attacking an entity that has what they need.

Exploitation of software supply chain vulnerabilities will be ongoing
Gartner predicts that by 2025, 45% of world orgs will have experienced an attack on their software supply chain, which is a 3x increase from 2021. 2023 brought us attacks at Okta, JetBrains, MOVEit, 3CX, Applied Materials, and lingering impacts from Log4j nearly 26 months later. These threats affected both private and public sector environments. Software supply chain attacks are likely to focus on open-source software. Open-source software is the foundation for tens of thousands of applications and services. However, open-source software is based on a largely decentralized approach combined with “inherent trust” from the industry and organizations. This makes it ripe as a potential target for threat actors.
Organizations should aim to shift away from a “how quick can we patch zero days” mentality to a “how do I properly secure this technology in the first place” approach. Rather than having an FTP server publicly exposed to everyone on the internet, how can we better reduce our attack surface by leveraging advanced authentication modules to open access to only those that need it, or harness zero-trust technologies to eliminate the need for public accessibility?
Critical infrastructure attacks will impact us all
We feel that as we look out on the horizon there is a looming storm beginning to take shape. We’ve dodged so many bullets over the years with critical infrastructure cyber attacks that it seems like our time is nearly up. Increased attack sophistication, attackers fueled by geopolitical tensions, weaponization of AI/ML, and thousands of critical infrastructure entities that can be easily compromised through legacy technologies or proprietary systems all increase the odds of major attacks. You do not need to look any further than the recent breach of six local water facilities compromised by having a Unitronics device accessible to the internet with a default password of 1111.
The shift of corporate responsibility to individuals is on
The recent SEC violations against SolarWinds, and explicitly the charges against the company and its CISO Timothy Brown, shed light on the potential shift in cybersecurity responsibility towards individuals, but it’s not a straightforward cause-and-effect relationship. However, the charges against Timothy Brown (highlighted here) reinforce that individuals will likely have more accountability. Our hope is that a shared responsibility model is operationalized, and we get away from shifting blame and the victim-blaming scenario.
CISOs, directors, VPs, and many more should push for a shared responsibility model in writing, simply and effectively communicate the organization’s cybersecurity risks to stakeholders frequently, and work toward putting themselves in a defensible position wherever possible.
Areas of clearer skies forecasted
Adoption of passwordless solutions gains traction
Passwordless solutions have been being discussed for years. Yet the adoption rate has been painfully slow. The reasons adoption rates have been dragging include things like legacy applications, user resistance, lack of interoperability, and costs. Passwordless technologies struggled with adoption, and, up until now, most of them hadn’t overcome these hurdles. Now, the majority of these issues have been resolved.
Here at Converge, we’re seeing more and more of our customers implement passwordless solutions, primarily through FIDO2, passkeys, and WebAuthn-only solutions. It’s likely that the adoption of passwordless technologies can dramatically reduce cybersecurity risks, such as traditional phishing attacks.
It is, however, important to understand how to choose the right passwordless solution. Organizations should focus on existing infrastructure and compatibility, security requirements and user preferences, and the scalability the technology provides.
Organizations will increasingly harness the power of AI to advance the maturity of detection and response automation
For 2024, we will likely see the progression of using AI technologies for more effective detection and response, in addition to truly automating response processes and procedures. There are likely no bigger contenders that will capitalize on AI more than security orchestration, automation, and response (SOAR).
While the advancements in cybersecurity AI technologies offer tremendous upsides for organizations, the downside is that organizations likely already have dozens of security controls living in their environments that offer AI capabilities that all live in disparate and siloed worlds.
With every major cybersecurity vendor offering some level of AI within their products, organizations need a way to centralize, operationalize, and capitalize all of them effectively. Many customers are reaching out to us for help with this challenge to leverage the amazing cybersecurity, analytics, and AI teams within the Converge organization.
DevSecOps picks up speed
If 2023 was the year we started to accelerate DevSecOps, 2024 is going to be the year we put the accelerator to the floor. GitLab produced an amazing global DevSecOps report that provides some tremendous insights:

|
71% of security professionals said at least a quarter of all security vulnerabilities are being spotted by developers, up from 53% in 2022. |

|
56% of respondents reported using DevSecOps methodologies, up from 47% in 2022 |

|
65% of developers said they are using AI and ML in security testing efforts or will be in the next three years. |
These statistics help support that the practice of shift left/everywhere is paying dividends in cost and time savings, easier automation, better collaboration, and, most importantly, better security. Organizations are also realizing that the advancements in AI/ML have a profound impact on application security. AI/ML now provides an effective ability to reduce application risk and help fight against what will likely be an increased attack focus on applications.
Stricter data privacy regulations protect us all.
2024 should show a significant tightening of data privacy rules and enforcement capabilities. Organizations will have to evolve their practices and comply with a much more intricate set of regulations. Florida, Oregon, Montana, Texas, and Delaware will see their comprehensive privacy laws go into effect throughout 2024. These laws grant consumers similar rights as California’s CCPA, such as access, correction, deletion, and opt-out of data sales.
Washington’s My Health My Data Act, set to take effect on March 31, will mark the beginning of this first US law specifically focused on health data privacy, regulating how it’s gathered, used, and disclosed. In the EU, the Digital Services Act (DSA) and Digital Markets Act (DMA) will apply to some companies starting in February 2024. The full range of obligations takes effect in March, further governing content moderation, data use for advertising, and user rights on online platforms.
Organizations should be laser focused on understanding how they will need to align to these state, federal, and global regulations. This can include enhancing data protection strategies, implementing new controls and countermeasures, and ensuring they are well prepared for the continued implementation of US and EU regulations.
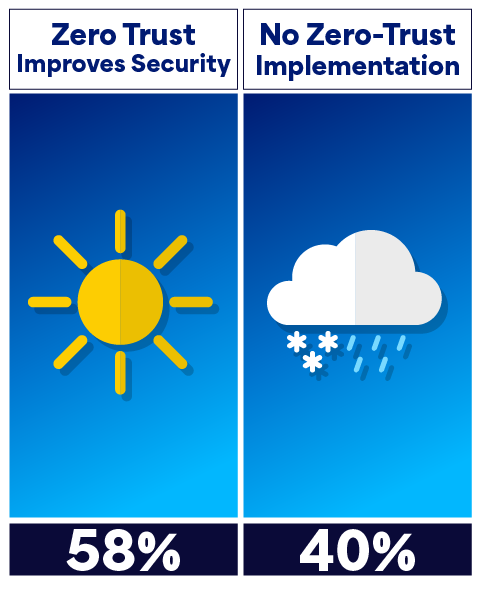
Adoption of zero trust continues throughout the year.
Zero trust is seen as improving security effectiveness by 58% of respondents to research by the Ponemon Institute, but almost 40% also say they haven’t implemented a zero-trust strategy.
While security leaders say there is value for the organization’s overall security with a zero-trust stance, more than 25% say their efforts to enact these are blocked by pushback from other business units. Those leaders who understand the value can use an incremental approach to get user buy-in.
There is no doubt that implementing a zero-trust framework can help reduce risk and increase visibility that further advances an organization’s detection and response maturity. To help overcome the challenges related to gaining support and budget for a zero-trust approach, start with the current state. Showcase the vulnerabilities of the existing security approach and the consequences of ransomware, breaches, or disruptions. Work to clearly explain the principles and value derived from using a zero-trust approach and how it can address the current state gaps and risks. Then, quantify the benefits. Using cost-benefit analysis can help show the anticipated reduction of attacks and breaches. Highlight how zero trust can help improve compliance. Identify how a well-executed zero-trust framework can actually enhance user experience. And, finally, be sure to include the notable increase in operational efficiency.
Data and experience improve preparation
Nobody can accurately predict what the future has in store. We’ve used a data-informed approach with quantitative and qualitative insights and our ongoing, extensive field experience to anticipate potential landscape changes. Being forearmed is a big part of the cyber battle and this information can help you implement effective preparatory measures.
We’re applying this same foresight to our products and services. Offerings that leverage AI and ML, apply zero-trust frameworks, and streamline cybersecurity operations are available now and more are in development:
- Application security
- Cybersecurity AI acceleration services
- Data privacy and data protection services
- DevSecOps framework implementation
- Passwordless assessment, design, and implementation services and solutions
- Penetration Testing as a Service (PTaaS)
- Ransomware assessment
- Security as a Service (SECaaS)
- Zero-trust readiness and implementation services and solutions
There are a lot of unknowns ahead, but joining forces with a progressive cybersecurity consultant can make all the difference in how prepared you are to face them. Connect with us today to learn more.