The quest for strong data security has all the elements of a cliffhanger Hollywood movie. Bad guys, good guys, treasure, chaos, and misadventure are all part of protecting data in a digital world. Businesses and organizations have data, bad guys want it, and nearly everyone creates and uses it. “Everything Data Everywhere All at Once” sounds like another award-show contender.
But this isn’t the movies and a simple plot twist won’t eliminate the risk and save the day. Instead, building a foundational data protection program has a beginning without an ending. A future-built data protection program adapts as your organization changes, allowing data security to alter and advance to meet new business objectives, technologies, and threats.
Why data protection matters
It’s a binary world, and cybersecurity professionals are just living in it…and duty-bound to protect it. Only 7% of Americans aren’t online. Similar results are likely for other developed countries.
That means the other 93% of us are online working, shopping, and interacting. A continuous flow of personal, critical, and sensitive information is shared, created, and used. Data is an asset that turns the wheels of modern commerce, from daily operation to innovation to competitive advantage. Data also fuels cyber-criminal enterprises.
Each year the cybersecurity industry waits for the latest reports to stun us with the rising price tag of a data breach, a figure currently estimated to average $4.35 million. While that number seems more likely to apply to a member of the Fortune 500, smaller businesses aren’t safer. They’re just hit with a proportionally smaller cost that may still be enough to put their viability at risk. A recent study shows that 57% of SMBs think they won’t be targeted, but almost 20% experienced an attack last year with an average cost of $108,000.
Protecting data in today’s enterprise
Modern communication spins on a data axis. A data protection program that saves data from loss, theft, and tampering won’t save the world, but it does help secure your organization’s corner of it by:
- Ensuring data is available and accurate. The cybersecurity triad of confidentiality, integrity, and availability is especially relevant to data. Ensuring that data is available when needed and accurate is crucial so businesses can rely on and trust data for informed business decisions.
- Improving organizational resilience. In the face of a cyber threat, businesses with secure data storage and current, effective data backups are better positioned to reduce risk and minimize impact in the event of a loss or breach.
- Meeting legal and compliance standards. Personal information, financial data, and other sensitive information can be used for nefarious purposes. Data in the wrong hands can lead to identity theft, financial fraud, and other types of cyber crime.
Protecting data isn’t just the ethical thing to do, it’s also essential for compliance. Regulations around data range from general protections, like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), to specific industry standards, such as the Health Information Portability and Accountability Act (HIPAA) and the finance industry’s Gramm-Leach-Bliley Act (GLBA) which requires protection of consumer data.
Failure to comply with applicable regulations can result in significant fines and penalties for out-of-compliance organizations.
- Preventing financial and reputational damage. The consequences of a data breach can be severe and long-term—damaging a company’s reputation and eroding customer trust. A significant financial impact from lost business, work stoppage, legal fees, and remediation efforts is likely.
Essentials for building a solid data protection foundation
Data protection is a large umbrella that includes data privacy, compliance, and data security. Ad hoc strategies built without the necessary scope can lead to gaps that increase risk. From creation to destruction, data is at risk of loss, corruption, and misuse.
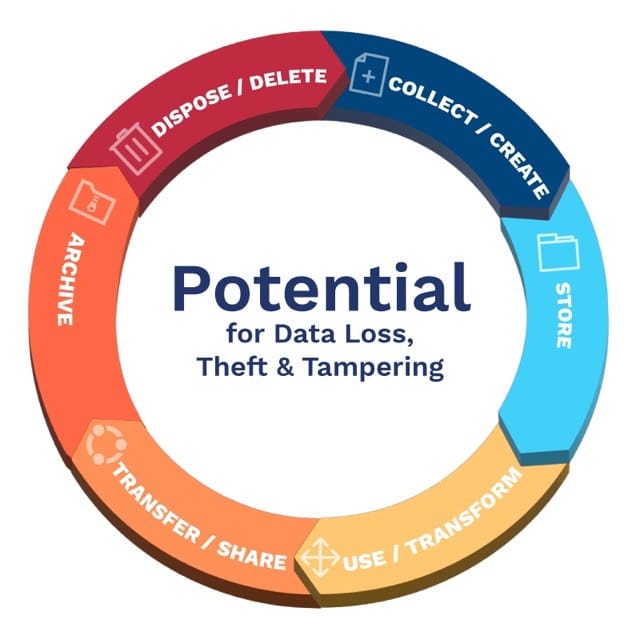
Starting with a foundational approach helps ensure that the necessary elements are in place for a continuous improvement process that protects data throughout the life cycle.
- Develop a data protection policy: Start by developing a comprehensive policy outlining your company’s data protection practices. Include details specific to the types and sensitivity of data collected, how it is stored, who has access to it, and how it will be protected.
- Build a program strategy: An effective data protection program requires a comprehensive strategy covering all aspects of data protection. This process helps you identify your organization’s data protection goals, assess current data protection requirements, and establish a roadmap for improvement.
- Train employees on data protection: Employees are often your first defense against data breaches. Create a culture of data security in your organization by helping users understand the value of data and what is at risk. Provide the necessary training so that they can identify risks and work with you to prevent them. Effective training should cover topics like password management, phishing scams, and how to handle sensitive data.
- Use encryption and other security technologies: Encryption is a powerful tool that can protect data in use, in transit, and at rest. Ensure that all sensitive data is encrypted and use security technologies like firewalls and intrusion detection systems to prevent unauthorized access.
- Use monitoring tools: Because of the risk to data throughout the life cycle, monitoring it in use, in motion, and at rest is vital. Data loss prevention (DLP) technologies or similar solutions automate the application of policies and protocols that monitor, detect, and block the malicious use and transmission of sensitive data.
- Implement data access controls: These controls help you determine who has access to your organization’s sensitive data to reduce the risk of unauthorized use. Role-based access controls, two-factor authentication, and other methods help ensure that each user has the necessary privileges, but no more.
- Have a data breach response plan: Preventing a data breach is the goal of your data protection program, but it can still happen. Planning for this possibility helps your organization minimize damage with a quick, effective response if an incident does occur.
- Have a disaster recovery plan: Disasters, from natural disasters like hurricanes and earthquakes to human-made disasters like cyber attacks and data breaches, can strike anytime. An important component of any data protection program, a disaster recovery plan helps ensure that critical data is protected and available even in the event of a disaster.
- Regularly review and update the data protection program: Data protection is an ongoing process that requires regular review and updates. Regularly assess your data protection program and make changes as needed to ensure that it remains effective.
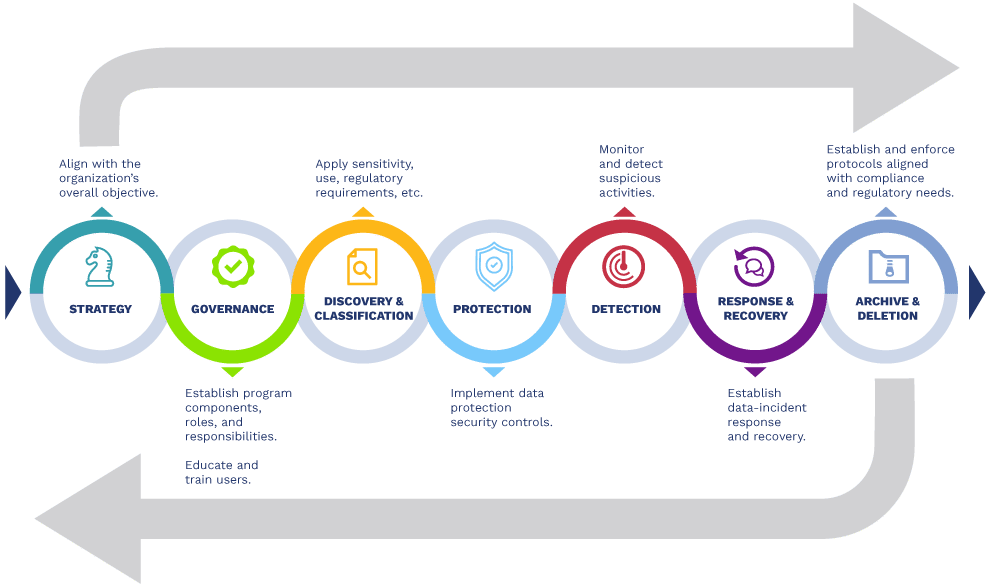
Putting the right data protection elements in place
Cloud and hybrid environments, expanded attack surfaces, changing compliance and regulations, and advancing user experiences simultaneously increase the need for and complicate the development of a data protection program.
A trusted partner can help you put data protection center stage in your organization and build a data security strategy aligned to your data privacy, security, and availability needs. Connect with us today if you’d like to learn more about our methodology, certifications, and experience.





