Software and application developers have a need for speed. Being first-to-market when it comes to products, services, and features has competitive advantages. To fast-track development, more organizations are combining methodologies, practices, and automation that outpace traditional development cycles.
CI/CD accelerates the development lifecycle
Implementing a continuous integration/continuous delivery (CI/CD) pipeline helps automate building, testing, and releasing code changes so that finding bugs is faster, user feedback is immediate, and updates happen more often.
Lean thinking and an agile environment are required, and developers need to embrace moving away from the more traditional process of full code release. It’s a cultural mind shift, and all stakeholders need to buy in.
Putting security into CI/CD
The global pandemic forced a rush to the cloud as business functions moved online to connect with customers and enable remote workers. Security was often unintentionally left in the dust.
Attackers rarely let a good vulnerability pass them by, and web applications are now prime targets. Converge’s Red Team reports a significant number of web app vulnerabilities discovered during our client testing engagements. Recent research shows that security is lagging in all areas of software development.
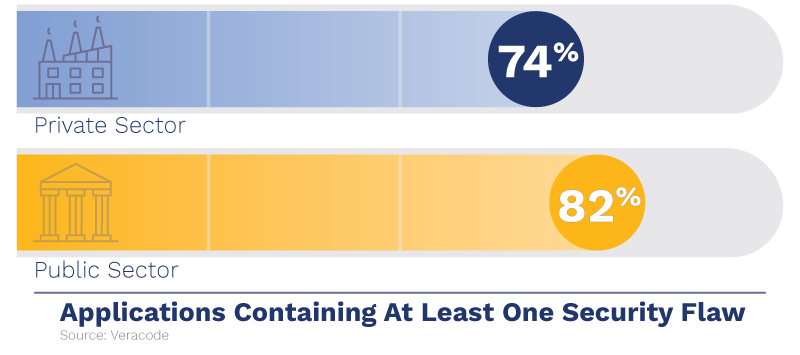
While 74% of private-sector applications have at least one security flaw, the public sector has an even higher risk at 82%.
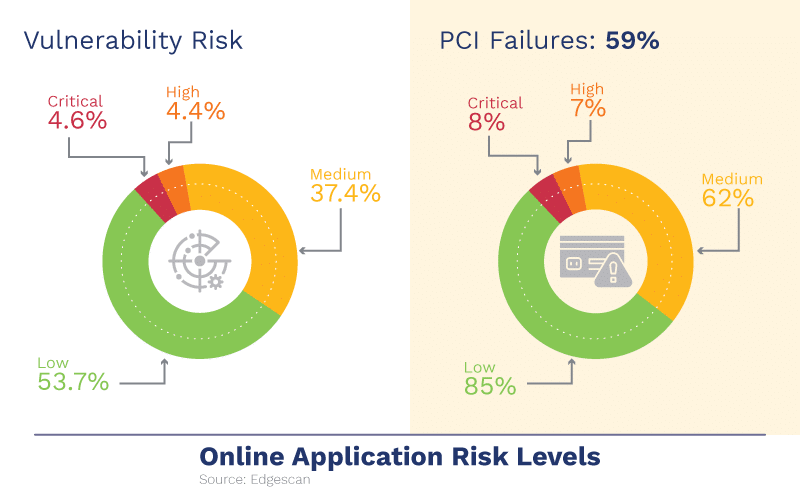
Not all vulnerabilities are created equally and additional findings show that 1 in 10 vulnerabilities in online applications are high or critical risk. The use of payment processing increased to 15%.
Applying a DevSecOps approach builds end-to-end security into your CI/CD pipeline and brings all participants together to ensure security is part of the full app development lifecycle. One of the more effective ways to do this is with ongoing, dynamic application penetration testing.
Smaller tests, more frequent testing
Automating processes is what makes CI/CD successful, and this includes some aspects of cybersecurity. There is a significant caveat to this, though. While automation tools can identify some vulnerability classes in infrastructure as code, they can’t spot traditional logic flaws. Missing those flaws can lead to session/state management vulnerabilities, code execution, and unauthorized data access due to improper permissions.
This important distinction supports the need for high-quality, dynamic penetration testing. By meshing application pen testing with the CI/CD process, it’s possible to “hack yourself first” with frequent tests sized for smaller feature sets added more often.
Security in tune with the CI/CD pipeline
After an initial penetration test of the entire application, smaller pen tests can be done on specific feature sets. This method reduces the time and cost of testing so that the CI/CD process doesn’t sacrifice security for speed.
Work with a security partner that helps you manage this process. Rapid, frequent testing can be challenging to track, remediate, and validate, but high-quality providers should be able to provide dashboards and management systems. Frequent requests for testing and retesting must be easy to submit so you can prioritize findings and remediation according to your smaller testing windows.
Build with security in mind
Shifting your app dev practice to include proactive testing on code changes in a staging or QA environment allows testing and remediation before releasing code to production.
This almost always saves time and money when vulnerabilities are identified early in the dev process. Vulnerabilities discovered in staging or QA pose significantly less risk and, in environments correctly configured, should pose no risk to users. The fewer times a development team needs change approval board (CAB) approval to push to production the better.
If your organization is shifting to a CI/CD pipeline, Converge can help you detect security gaps before production. Our experienced testers use sophisticated, hands-on methods and leading tools, and your test results and fix recommendations are delivered quickly through an online portal. Contact us today to learn more or to get started.