“The changing threat landscape…” That phrase gets a lot of mileage in the cybersecurity industry. It is a simple truth that seems to require more and more complicated responses. You can clear the haze and put core security essentials back into focus with the Center for Internet Security (CIS) Critical Security Controls.
There are 18 CIS Critical Security Controls (CIS Controls) that most cybersecurity frameworks, standards, and guidelines use as a base. Understanding these controls and how they connect to your cybersecurity program makes it easier to decode a response to shifts in technology solutions, emerging threats, and your environment.
What are the 18 CIS Controls?
The CIS Critical Security Controls offer a clear, ordered, and straightforward collection of best practices for enhancing your cybersecurity stance. Global cybersecurity professionals utilize and/or aid in shaping the CIS Controls through a collective agreement method.
The guiding purpose of this list of controls is to provide prioritization that helps businesses quickly determine the best path toward building an organization’s defensible cybersecurity position. As the “Rosetta Stone” for other measures and methods, the controls don’t cover every use case, but they help re-center on cybersecurity’s true north priorities.
- Inventory and Control of Enterprise Assets
- Inventory and Control of Software Assets
- Data Protection
- Secure Configuration of Enterprise Assets and Software
- Account Management
- Access Control Management
- Continuous Vulnerability Management
- Audit Log Management
- Email and Web Browser Protections
- Malware Defenses
- Data Recovery
- Network Infrastructure Management
- Network Monitoring and Defense
- Security Awareness and Skills Training
- Service Provider Management
- Application Software Security
- Incident Response Management
- Penetration Testing
Thinking of all 18 controls as a connected mesh or honeycomb helps visualize the CIS domains. When a domain is weak or lacking in coverage, it creates a gap that weakens the overall structure. The first eight, shown in the lighter blue, are considered foundational and will determine the overall success of an organization’s ability to identify and remediate cybersecurity threats.
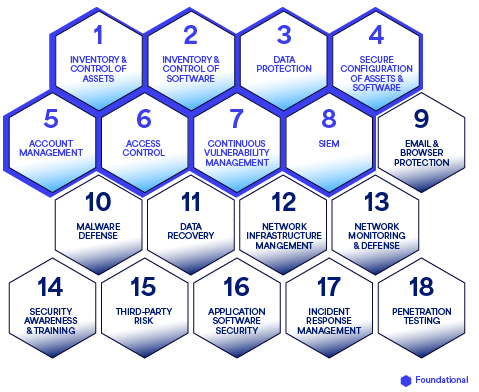
Mapping security priorities with CIS controls
It’s a straightforward list that includes essential areas. Ending up in a good, defensible position to thwart current cybersecurity threats means getting each area right before moving on to the next.
Knowing how the controls interconnect makes the process more straightforward and allows organizations to comprehensively address areas that build the firm foundation needed to move to the next area.
We group controls applying logic like that needed to be a safe driver. The car needs to be sound, the passengers need to be safe, the driver needs to be aware and alert, the roads need to be in good condition, and other drivers need to be considered.
Ensuring correct management, configuration, and scanning of assets
Protecting data
Developing visibility, awareness, and preparedness across all domains

Protecting endpoints and communication channels

Guarding and monitoring the network
Managing third-party risk

Securing application development

Connecting CIS controls to your security program
Grouping the controls makes it easier to understand the relevant security areas and to prioritize the next steps.
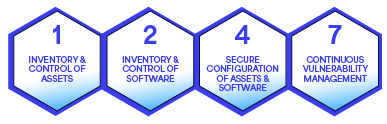
- Asset management with Controls 1, 2, 4 and 7
Ensuring that you know your assets and that they are correctly configured and managed is the cornerstone for building an effective program. In the spirit of our driving analogy, this area establishes that the car is roadworthy.
The primary focus here is software and hardware. While data is a critical asset, we use a different control grouping to address those safeguards. This area dials in on ensuring that software configurations are correct, that endpoints are protected, that you have a current asset inventory, and that continuous vulnerability scanning processes keep asset protection and configuration current.
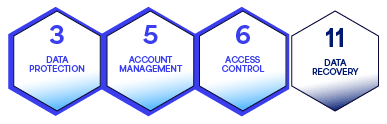
- Data protection with Controls 3, 5, 6, and 11
Once the network assets are protected, you are ready to protect what will travel that network. Data is your environment’s most valuable and vulnerable element and requires protection at all points of the journey.
Data needs to be identified and classified to protect it at the appropriate level. You need to know where it is, who or what is accessing it, and how to recover it.
- Network visibility and awareness with Controls 8, 17, and 18
What you see and hear impacts your reactions on the road. The same is true for your network. A security incident and event management (SIEM) solution monitors and listens to your network through the data gathered and fed into it.
A properly optimized and configured SIEM provides continuous real-time diagnostics, detecting anomalies in the patterns of your network and providing prioritized alerts to let you know when an issue needs your attention.
- Endpoint and communication channel safeguards with Controls 9, 10, and 14
Managing what gets in and out of your organization through endpoints and communication channels includes managing email and web browser activity and security.
These essential productivity tools are heavily targeted attack vectors, providing direct conduits to users. Users need training on safe practices and awareness of the risks and tactics used, and both users and systems must be protected from attacks that deliver malicious payloads and malware through emails and online activity.
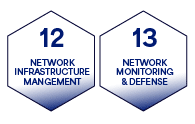
- Traffic management with Controls 12 and 13
Anything moving across the network needs monitoring. Like roadways, networks need moderation of traffic flow and guardrails to prevent negative impacts.
Maintaining network health and security involves reacting to and remediating traffic jams, infrastructure weaknesses, and incidents.
- Directing third-party risk with Control 15
No organization operates in a bubble. Third-party, fourth-party, and partner security practices directly correlate to your organization’s risk. It’s a complex area, and identifying the web of related parties your company engages with requires a multilayered approach.
Distilled to its most straightforward equation, managing vendor and partner risk involves knowing and managing access between them and your data, users, and systems.
- Securing application development with Control 16 (optional)
This control can be optional in the sense that it applies to companies that focus on the development of software-based applications. This control is essential if your organization develops applications for internal or external use.
Implementing DevSecOps processes to secure the software development lifecycle is crucial to minimize the risk and impact on your organization from insecure code.
Using CIS security controls to advance your security program
Most regulations and methodologies, including a myriad of separate yet similar frameworks, guidelines, and requirements, branch from these core controls. A solid understanding of the CIS Critical Security Controls translates into better insight into the frameworks and regulations specific to your organization.
Converge uses these controls to help customers understand their environments. We assess each domain and its associated controls, identify strengths and gaps, and then create a heatmap that prioritizes risks, actionable recommendations, and next steps.
If you’d like to develop a cybersecurity roadmap based on an assessment of your organization’s adoption of the CIS Critical Security Controls, contact us today for a free consultation.





